By Erol Gelenbe, Institute of Theoretical and Applied Informatics of the Polish Academy of Sciences (IITIS-PAN)
The IITIS-PAN team has obtained some recent results as part of the DOSS project, regarding the analysis of the behaviour of real (non-virtual) IoT Gateways, in order to determine the salient features of these systems when cyberattacks occur. The motivation for this work resides in the need to identify the characteristic behaviour of Gateways for the purpose of building their Digital Twins, so that one may faithfully reproduce the effects of normal and attack traffic on a Gateway.
This work has required the laboratory construction of a typical Gateway system that includes emulators of sensors/actuators, using Raspberry Pi processors, connected to an Ethernet switch to represent an IoT interconnection network, and an eight-core workstation supporting the network access to and from the sensors/actuators, an Intrusion Detection System (IDS) based on the Deep Random Neural Network to provide high accuracy detection of malicious packets. Between the Ethernet switch and the Gateway, we have also experimented with the placement of a smart Quasi-Deterministic Traffic Policy forwarder (SQF) that shapes the input traffic to attenuate the effect of attacks on the Gateway.

Figure 1 Network Architecture where the Server is protected by a novel QDTP Smart Forwarder
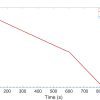
Extensive measurement results, some of which are reported in a recent paper which won the best paper award at IEEE Trustcom2023 [1], detail the histograms of the packet processing times (or overhead created by the IDS) with and without attacks. They show that the high processor overload that is due to the numerous incoming packets at the Gateway when an attack occurs, causes the IDS packet processing time histograms with and without an attack, will differ substantially, with a substantial increase in processing times under attack that shows a heavy-tailed behaviour. This also causes substantial slowdowns and the build-up of very large packet queues at the entrance of the Gateway. Our measurements also show that the use of the SQF at the entrance of the Gateway will allow packets to accumulate at its own input, and hence protect the Gateway and allow the IDS to operate normally. In a related mathematical development, we also prove that the SQF does not increase the end-to-end delay for packets arriving from the IoT devices to the Gateway, either during « normal » or « attack » modes of operation so that the SQF has no negative operational effects.

Figure 2 Server’s Input Queue Length Without (High) and With (Low Blue) the Smart Forwarder after a 10 second Flood Attack
These results indicate that the DOSS Digital Twin approach will need to incorporate such effects and that they could be included by using a high-level modelling approach such as large deviations (from probability and statistics) to predict the overload effects of attacks.
[1] E. Gelenbe and M. Nasereddin, « Protecting IoT Servers Against Flood Attacks with the Quasi Deterministic Transmission Policy » (Best Paper Award, IEEE Trustcom 2023), The 22nd IEEE International Conference on Trust, Security and Privacy Computing and Communications, November 2023, Exeter, UK, IEEEXplore, January 2024, pp. 1-8.